Investigate how websites, apps, and digital platforms collect user data — and how you can protect yourself.
Introduction
In an era where our lives are increasingly lived online—from social networking to shopping, streaming to banking—our personal data has become one of the most valuable commodities. But how much of your data is truly safe? The reality is far more complex and concerning than most realize. At TrueReports, we dive deep into the digital underworld to reveal how websites, apps, and platforms harvest, use, and sometimes exploit your data — often without your full knowledge or consent.
This article explores the mechanisms of data collection, the risks involved, the realities of data breaches, and most importantly, actionable steps you can take to safeguard your privacy in an interconnected world.
1. The Digital Footprint: What Data Are You Really Sharing?
1.1 More Than You Think
Every interaction online leaves a digital trace. From the moment you open an app or visit a website, data points about you start accumulating:
- Personal Identifiers: Name, email, phone number, address.
- Behavioral Data: What pages you visit, how long you stay, clicks, scrolls.
- Device Information: IP address, device type, operating system, browser version.
- Location Data: GPS coordinates, Wi-Fi signals, cell tower triangulation.
- Communication Data: Messages, emails, call logs (in some apps).
- Biometric Data: Face scans, fingerprints, voice patterns (in advanced apps).
- Purchase History: What you buy, how often, how much you spend.
- Social Interactions: Likes, shares, comments, friend connections.
This data can be collected actively (you enter it) or passively (automatically tracked).
1.2 The Data Ecosystem: Who Has Your Info?
- First-Party Collectors: The apps and websites you directly interact with.
- Third-Party Trackers: Advertisers, analytics services, social media plugins embedded in sites.
- Data Brokers: Companies that aggregate and sell consumer data to marketers, insurers, lenders.
- Hackers & Fraudsters: Illicit actors who steal data through breaches or phishing.
2. How Websites and Apps Collect Data
2.1 Cookies and Tracking Pixels
Cookies are small text files stored on your device that remember preferences but can also track behavior across sites. Tracking pixels are tiny, invisible images embedded in emails or web pages that notify the sender when you open or interact.
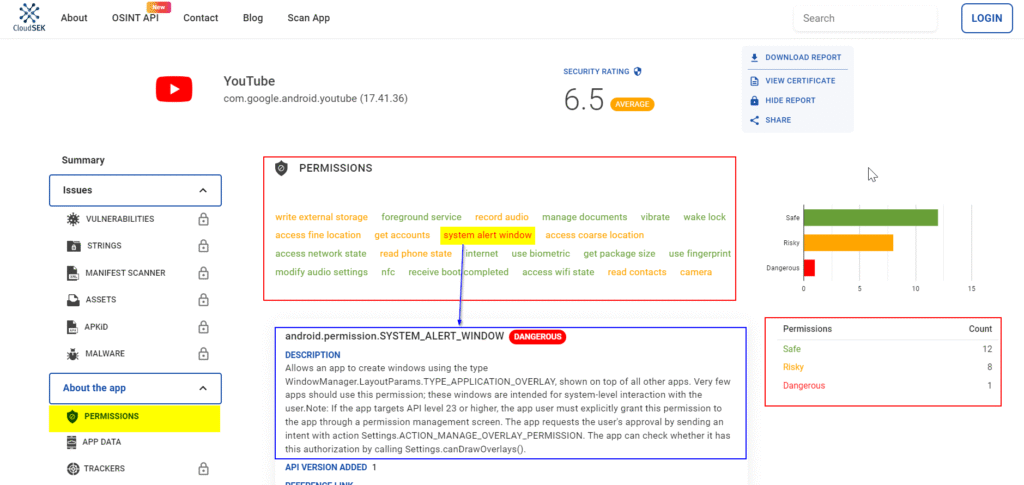
2.2 Mobile App Permissions
Apps often request permissions that grant access to contacts, camera, microphone, location, storage, and more. Some of these are essential for functionality, but others enable extensive data harvesting.
2.3 Browser Fingerprinting
Beyond cookies, websites can gather unique device and browser characteristics—such as installed fonts, screen resolution, and timezone—to create a “fingerprint” that tracks you even if cookies are blocked.
2.4 Social Media Integrations
“Like” buttons and embedded feeds let social platforms collect data on non-users too, tracking visits and interactions on third-party sites.
2.5 Data Collection Examples
- Google’s vast ad network tracks users across millions of sites.
- Facebook’s Pixel tracks user behavior off-platform for targeted ads.
- Apps like TikTok and Instagram collect facial recognition data and detailed usage patterns.
- Retailers analyze purchase and browsing history to personalize offers.
3. The Dark Side: Data Breaches and Privacy Violations
3.1 Alarming Statistics
- Over 4.5 billion records were exposed in data breaches globally in 2023 alone.
- Major breaches include consumer giants like T-Mobile, Facebook, and Equifax.
- Many breaches go unreported or are discovered months later.
3.2 Consequences for Individuals
- Identity Theft: Criminals use stolen data to open credit lines or file fraudulent tax returns.
- Financial Loss: Unauthorized purchases or loans in your name.
- Reputation Damage: Sensitive information leaked publicly.
- Privacy Invasion: Stalking, harassment, or blackmail using leaked personal info.
3.3 Case Study: The Equifax Breach
In 2017, Equifax, one of the largest credit bureaus in the U.S., suffered a breach exposing sensitive data—names, social security numbers, birth dates—of over 147 million people. The fallout included costly lawsuits, regulatory scrutiny, and ongoing concerns over the misuse of this data.

4. Regulations and Your Rights
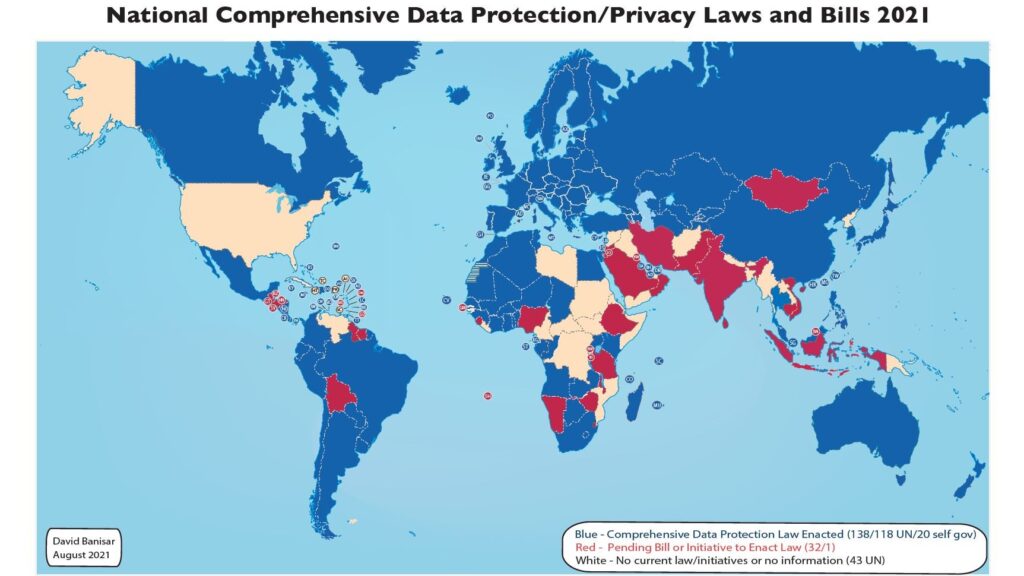
4.1 Global Privacy Laws
- GDPR (Europe): Gives users rights to access, correct, and delete their data; requires explicit consent.
- CCPA (California): Grants rights to know, delete, and opt-out of sale of personal information.
- Other Jurisdictions: Many countries are adopting or updating privacy regulations (e.g., Brazil’s LGPD, India’s PDP Bill).
4.2 What These Laws Mean for You
- Right to know what data is collected and how it’s used.
- Right to refuse or revoke consent.
- Right to request data deletion (“right to be forgotten”).
- Companies must notify users in case of breaches.
4.3 The Gaps in Regulation
- Enforcement varies widely; many companies still operate with minimal oversight.
- Complex privacy policies obscure true practices.
- Cross-border data flows complicate jurisdiction.
5. How You Can Protect Your Data: Practical Tips
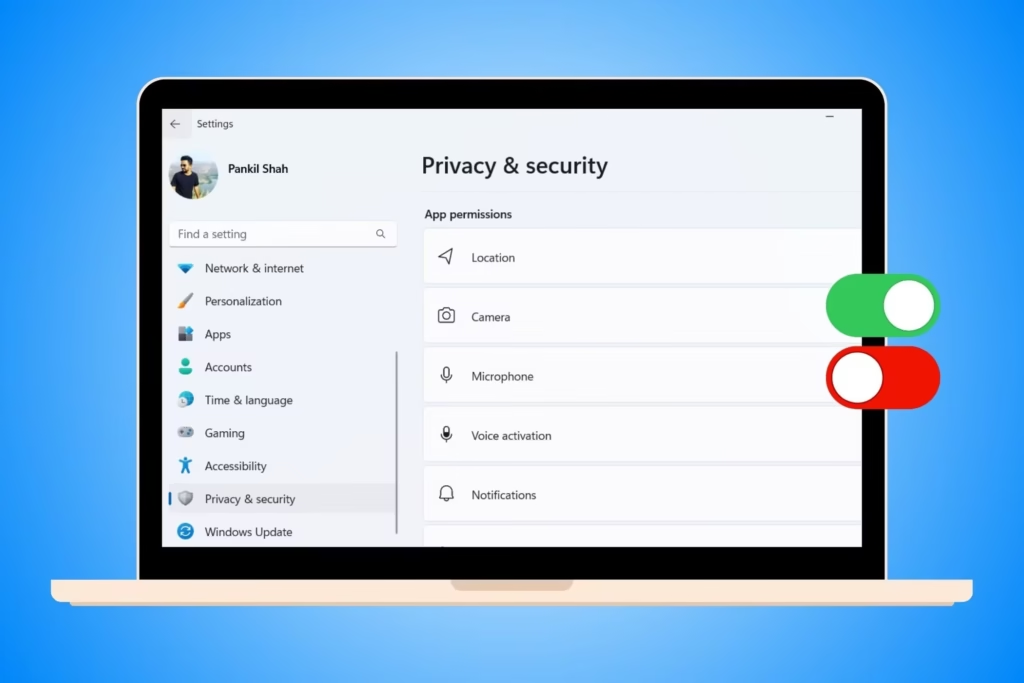
5.1 Be Vigilant with Permissions
- Only grant app permissions that are essential.
- Regularly audit app permissions on your devices.
5.2 Use Privacy-Focused Tools
- Browsers like Brave or Firefox with enhanced tracking protection.
- VPNs to mask IP addresses and encrypt traffic.
- Encrypted messaging apps (Signal, Telegram).
5.3 Manage Cookies and Trackers
- Clear cookies regularly or use browser settings to block third-party cookies.
- Use tracker-blocking browser extensions (uBlock Origin, Privacy Badger).
5.4 Strong Password Hygiene
- Use long, unique passwords per site.
- Employ password managers (LastPass, 1Password).
- Enable two-factor authentication (2FA) wherever possible.
5.5 Think Before You Share
- Be cautious about what you post on social media—once online, data is hard to erase.
- Review privacy settings on social platforms.
6. The Future of Privacy: Trends and Technologies
6.1 Decentralized Identity Solutions
Blockchain and decentralized ID projects aim to give users control over their personal data, sharing only what is necessary.
6.2 AI and Privacy
While AI can improve security (anomaly detection), it also poses risks—deepfakes, data profiling, and surveillance.
6.3 Privacy-Enhancing Technologies (PETs)
Homomorphic encryption, differential privacy, and federated learning promise data analysis without exposing raw data.
7. The Ethical Dimension: Who Should Control Data?
7.1 Corporate Responsibility
Companies must prioritize ethical data practices, transparency, and user consent—not just compliance.
7.2 Consumer Empowerment
Awareness, digital literacy, and advocacy can shift the power balance toward individuals.
8. Real Stories: How Data Loss Affected People
8.1 Identity Theft Nightmare
Sarah, a working mother, lost thousands to credit card fraud after a data breach exposed her info. The recovery took months and caused emotional distress.
8.2 Social Media Overexposure
James shared vacation photos publicly; scammers used location data to attempt burglaries at his home.
9. Myths and Misconceptions About Online Privacy
- “Incognito mode keeps me completely anonymous.” — False; it only prevents local browsing history storage.
- “Small websites don’t track me.” — False; third-party trackers often embedded even in small sites.
- “I have nothing to hide.” — Privacy is about control and safety, not just hiding wrongdoing.
Conclusion
Your data is valuable, and in the digital age, privacy is fragile. Understanding how your information is collected and used is the first step toward reclaiming control. While no system is foolproof, adopting smarter habits, leveraging privacy tools, and demanding stronger protections can help secure your digital life.
At TrueReports, we believe informed users are empowered users. Stay vigilant, question the platforms you trust, and protect your digital self fiercely.
Appendix: Useful Privacy Resources
- Electronic Frontier Foundation (EFF) – https://www.eff.org/
- Privacy Rights Clearinghouse – https://privacyrights.org/
- Data & Society Research Institute – https://datasociety.net/
- StaySafeOnline – https://staysafeonline.org/
- Browser Extensions: uBlock Origin, Privacy Badger, HTTPS Everywhere
